Current Projects
- SaTC: CORE: Small: Semantics-Oriented Binary Code Analysis Learning from Recent Advances in Deep Learning, PI: Lannan Luo (Solo PI), National Science Foundation (NSF), $416,947, 2020-2023.
- CRII: SaTC: A Malware-Inspired Approach to Mobile Application Repackaging and Tampering Detection, PI: Lannan Luo (Solo PI), National Science Foundation (NSF), $174,879, 2019-2021.
- SaTC: CORE: Small: Collaborative: Enabling Precise and Automated Insecurity Analysis of Middleware on Mobile Platforms, PIs: Lannan Luo, Qiang Zeng, and Peng Liu (Penn State University), National Science Foundation (NSF), $159,000, 2018-2021.
- Vulnerability Discovery and Test Input Generation for Android System Services, Lannan Luo (Solo PI), USC ASPIRE-I, $14,994, 2018-2019.
Past Projects
- Centaur: Symbolic Execution of Android Framework with Application to Exploit Generation (MobiSys'17)
- SSN: Repackage-proofing Android Apps (DSN'16)
- SolMiner: Mining Distinct Solutions in Programs (ICSE-SEET'16)
- Algorithmic Plagiarism Detection (TSE'17)
- CoP: A Binary-Oriented Obfuscation-Resilient Software Plagiarism Detection Approach (FSE'14, TSE'17)
Software Release
- Centaur: Symbolic Execution of Android Framework for Vulnerability Discovery and Exploit Generation (MobiSys'17)
Centaur: Symbolic Execution of Android Framework with Application to Exploit Generation
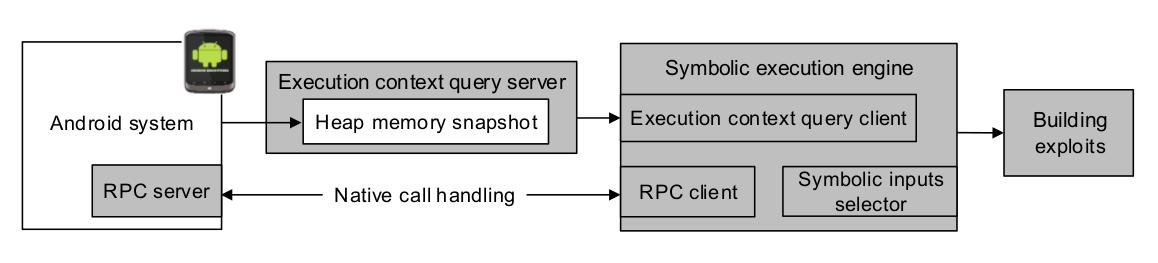
Android Framework is a layer of software that exists in every Android system managing resources of all Android apps. A vulnerability in Android Framework can lead to severe hacks, such as destroying user data and leaking private information. With tens of millions of Android devices unpatched due to Android fragmentation, vulnerabilities in Android Framework certainly attract attackers to exploit them. So far, enormous manual effort is needed to craft such exploits. To our knowledge, no research has been done on automatic generation of exploits that take advantage of Android Framework vulnerabilities.
We make a first step towards this goal by applying symbolic execution of Android Framework to finding bugs and generating exploits. We have built the first system for symbolic execution of Android Framework. It fundamentally changes the state of the art in exploit generation on the Android system, and has been applied to constructing new techniques for finding vulnerabilities.
Related Publications:
| MobiSys 2017 |
"System Service Call-oriented Symbolic Execution of Android Framework with Applications to Vulnerability Discovery and Exploit Generation" Lannan Luo*, Qiang Zeng*, Chen Cao, Kai Chen, Jian Liu, Limin Liu, Neng Gao, Min Yang, Xinyu Xing, and Peng Liu (*Co-first authors). In Proceedings of the 15th ACM International Conference on Mobile Systems, Applications, and Services (MobiSys), Niagara Falls, NY, June 19th-23rd, 2017. >> [PDF] |
SSN: Repackage-proofing Android Apps
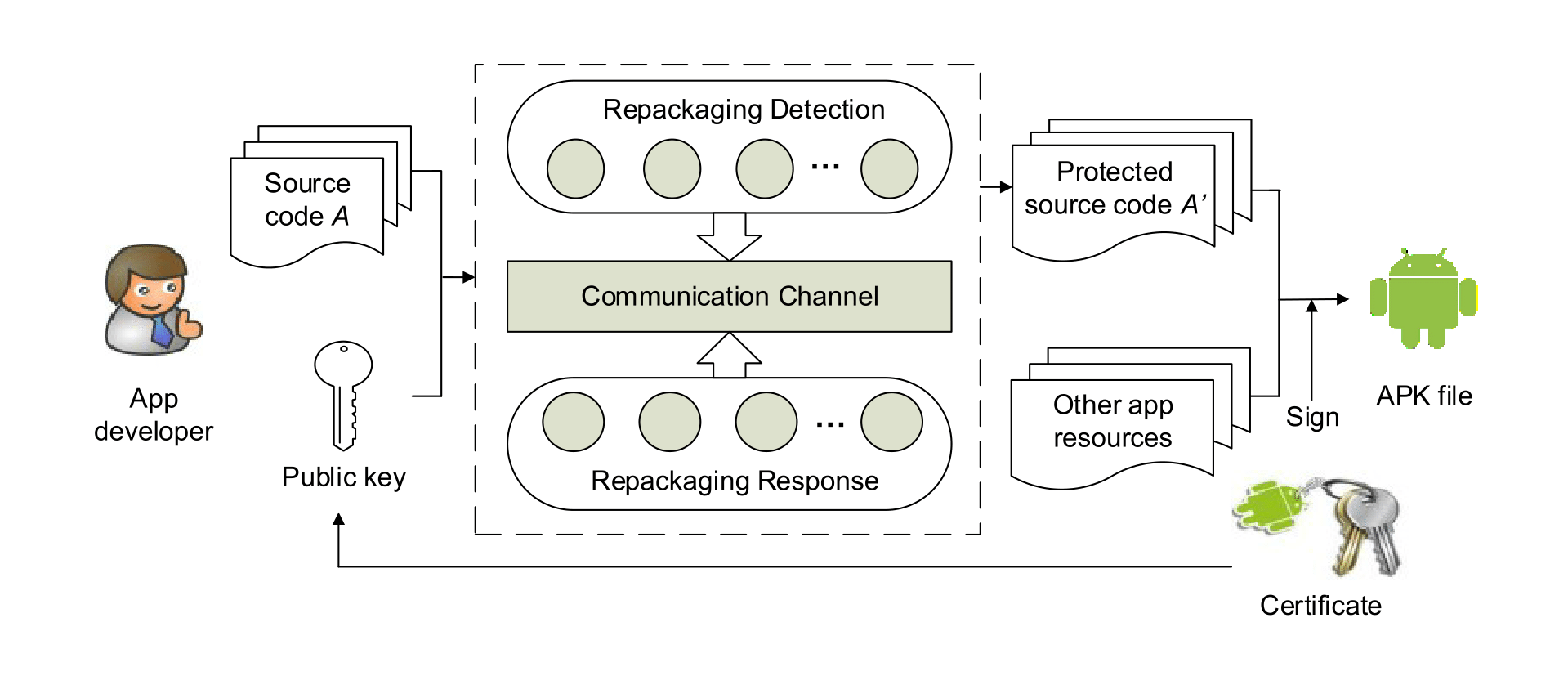
App repackaging has become a severe threat to the Android ecosystem. While various protection techniques, such as watermarking and repackaging detection, have been proposed, a defense that stops repackaged apps from working on user devices, i.e., repackage-proofing, is missing. We propose a technique that builds a reliable and stealthy repackage-proofing capability into Android apps. We have built a prototype. The evaluation shows that the technique is effective and efficient.
Related Publications:
| DSN 2016 |
"Repackage-proofing Android Apps." Lannan Luo, Yu Fu, Dinghao Wu, Sencun Zhu, and Peng Liu. In Proceedings of the 46th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN), Toulouse, France, June 28-July 1, 2016. >> [PDF] |
SolMiner: Mining Distinct Solutions in Programs
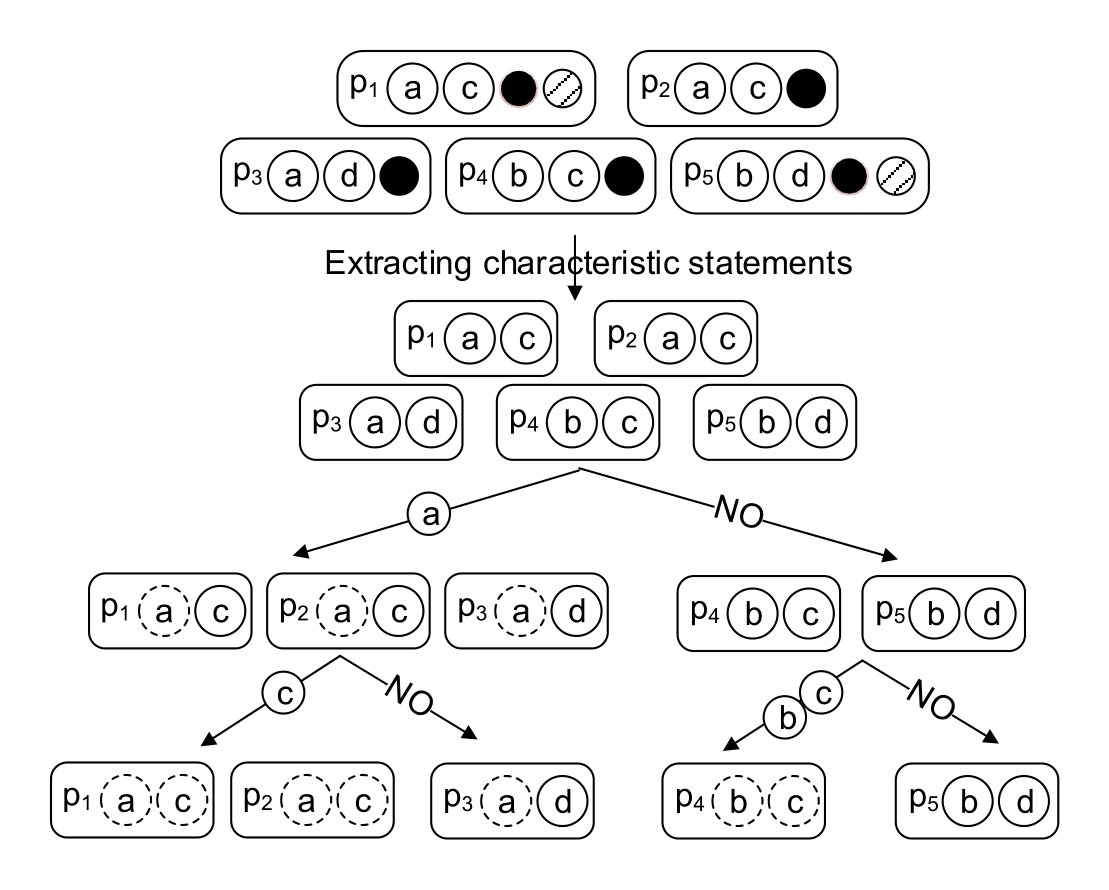
On the Internet many websites provide venues for programming practice and contests. While these websites can automatically judge the correctness of a submission, none extracts distinct solutions from the submissions and provides them to learners. How to automatically identify distinct solutions from a large number of submissions is a challenging and unresolved problem. Due to diverse coding styles and high programming flexibility, submissions implementing the same solution may appear very different from each other; in addition, dealing with submissions at scale imposes extra challenges.
We propose SolMiner, a solution miner, that automatically mines distinct solutions from a large number of submissions. SolMiner leverages static program analysis, data mining, and machine learning to automatically measure the similarity between submissions and identify distinct solutions. We have built a prototype of SolMiner and evaluated it. The evaluation shows that the technique is effective and efficient.
Related Publications:
| ICSE-SEET 2016 |
"SolMiner: Mining Distinct Solutions in Programs." Lannan Luo, and Qiang Zeng. In Proceedings of the 38th International Conference on Software Engineering (ICSE), SEET, Austin, TX, May 14-22, 2016. >> [PDF] |
Algorithmic Plagiarism Detection
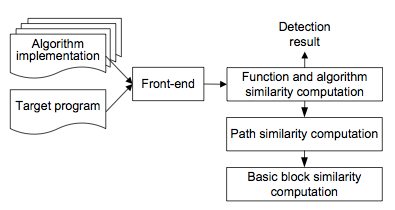
Identifying an algorithm directly in binary code has many important applications. For example, one application is to detect intellectual property infringement that a protected algorithm presents in a software product without proper license. Another application is to detect cryptographic algorithms which have been increasingly employed by modern malware to circumvent detection, hide network communications, and protect payloads among other purposes. In this project, we develop a semantics-based binary-oriented obfuscation-resilient tool to automatically identify algorithms within binary code. We have developed a prototype. In evaluation, our tool successfully detected the present of six cryptographic algorithms in thirteen benchmark programs ranging from small to large real-world production software.
Related Publications:
| TSE 2017 |
"Semantics-Based Obfuscation-Resilient Binary Code Similarity Comparison with Applications to Software and Algorithm Plagiarism Detection" Lannan Luo, Jiang Ming, Dinghao Wu, Peng Liu, and Sencun Zhu. IEEE Transactions on Software Engineering (TSE), 2017. >> [PDF] |
CoP: A Binary-Oriented Obfuscation-Resilient Software Plagiarism Detection Approach
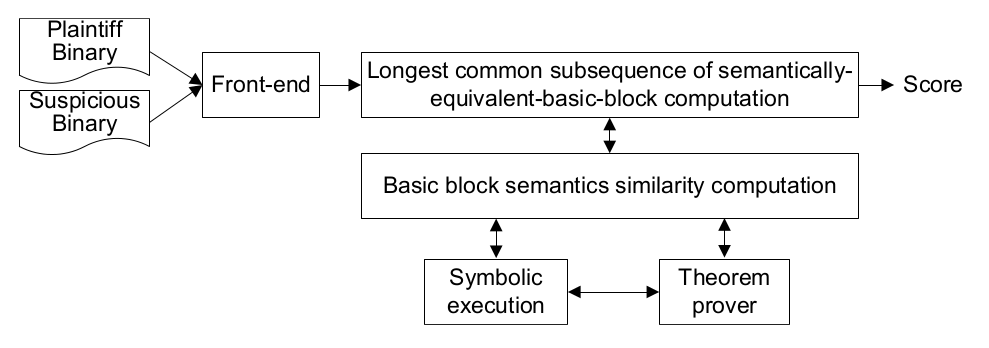
Existing code similarity comparison methods, whether source or binary code based, are mostly not resilient to obfuscations. In the case of software plagiarism, emerging obfuscation techniques have made automated detection increasingly difficult.
In this project, we propose a binary-oriented, obfuscation-resilient method based on a new concept, longest common subsequence of semantically equivalent basic blocks, which combines rigorous program semantics with longest common subsequence based fuzzy matching. We model the semantics of a basic block by a set of symbolic formulas representing the input-output relations of the block. This way, the semantics equivalence (and similarity) of two blocks can be checked by a theorem prover. We then model the semantics similarity of two paths using the longest common subsequence with basic blocks as elements. This novel combination has resulted in strong resiliency to code obfuscation.
We have developed a prototype and our experimental results show that our method is effective and practical when applied to real-world software.
Related Publications:
| FSE 2014 |
"Semantics-Based Obfuscation-Resilient Binary Code Similarity Comparison with Applications to Software Plagiarism Detection." Lannan Luo, Jiang Ming, Dinghao Wu, Peng Liu, and Sencun Zhu. In Proceedings of the 22nd ACM SIGSOFT International Symposium on the Foundations of Software Engineering (FSE), Hong Kong, China, November 16-22, 2014. >> [PDF] |
| TSE 2017 |
"Semantics-Based Obfuscation-Resilient Binary Code Similarity Comparison with Applications to Software and Algorithm Plagiarism Detection" Lannan Luo, Jiang Ming, Dinghao Wu, Peng Liu, and Sencun Zhu. IEEE Transactions on Software Engineering (TSE), 2017. >> [PDF] |